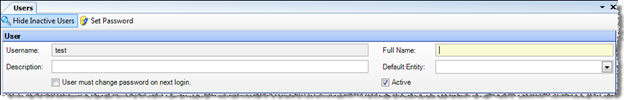
The Users screen lets you define and manage the application's users. This includes specifying which entities each user can access, and which groups each user belongs to.
Note: Remember that it is each user's membership in a group that determines which menu options are available.
Each user must be assigned to at least one group. If a user is not assigned to a group, the user ID cannot be saved; therefore, you must define your groups before you define users.
The header fields in the top of the Users screen allow you to enter basic information about the user. Once you have completed these, either save the user and create a password or proceed to assign group membership and entity access.

To create a new user, select New Record
![]() from the main toolbar and fill in the following
fields:
from the main toolbar and fill in the following
fields:
Username Enter a user name for the user.
Full Name Optionally enter the user's full name.
Description Optionally enter a description for the user, such as a job title.
Default Entity Optionally select a default entity. This entity will be used as the default when a user logs in. Users will still have the option to change the entity.
User must change password Check to require user to change password on subsequent login. This is generally used when you set up an account for someone else.
Active When checked indicates that a user will be able to login with the Username. When unchecked indicates the user is inactive and will be prohibited from logging into system.
Click Save ![]() to save the user definition.
to save the user definition.
Before the user is saved, you will be prompted to create a password. The user will be added to the Compeat database.
The login method you opt for will determine if you need to add users to SQL Server or not.
There is basically a trade-off between better performance using LAN and better security using Remote Access.
Users can log into Compeat in one of two ways, with Remote Access or
with LAN Access. Users who access Compeat from outside of the home office
via the internet have to use Remote Access. For users who are at the home
office, they can choose either method. The recommended access method for
most users is Remote Access as it provides better security. If you have
users on a LAN and are not concerned about them being able to access Compeat
data from outside of the application, then LAN Access may be best. The
following table compares features of each method:
Descriptions |
Remote Access |
LAN Access |
Access software outside of home office network |
Yes |
No |
Access software inside of home office network |
Yes |
Yes |
Access Compeat data from outside application using standard query tools |
No |
Yes |
Highest Possible Performance |
No |
Yes |
Login password stored in/validated against Compeat database |
Yes |
No |
Login password stored in/validated against SQL Server |
No |
Yes |
When new users are created, their user names and passwords will initially only exist in the Compeat database and they will only be able to access the system using Remote Access. This is the most secure method. If you wish to grant LAN access to a user, click the Add User to SQL Server button. This will give that user an account on SQL Server and enable them to log in by choosing the LAN Access method. Users with a SQL Server account can also access all Compeat data outside of Compeat using standard query tools.
Note: To create a new user on SQL Server, you must be logged in as a SQL Server administrator if you are connected through a LAN; if you are logged on through the data portal, you will have administrative rights. For information on how to do this, contact your system administrator or Compeat Technical Services.
The password set here is what the user will use to log into the system. If the user has already been added to SQL Server, both the Remote Access password (stored in the Compeat database) and LAN Access password (stored in SQL Server) will be updated.
Your Compeat password must be at least 6 characters long, with at least 1 non-alphabetic character.
Users who do not have access to this screen can be given a lower level security access to change their passwords in the Change Password screen under the Utilities menu.
When a user belongs to multiple security groups, the screen access of those groups is cumulative. That is to say, the user has access to each screen any one of his group definitions allows.
Restrictions to particular inventory level definitions and vendor groups, if used, are also cumulative in the sense that the restrictions of any one group definition will apply to that user.
Example:
Say that Tom belongs to both the Administrators
group and the Bar Managers group.
The Administrators group has no inventory level or vendor group restrictions;
while the Bar Managers group restricts its users to the Alcohol inventory
level definition. Tom will only be able to see Alcohol inventory until
such time as he removes his membership in the Bar Managers group.
Finally, in the case where a user belongs to multiple groups, with inventory level and/or vendor group restrictions in more than one group definition, the user will be able to access each level definition and vendor group to which the various group definitions are restricted. In the above example, if the Administrators group were to restrict its users to the Office Supply inventory level definition, Tom would be able to see Office Supply and Alcohol inventory.